Cyber Security Career Training Program
Orange ITech Provide’s 100% Placement Assistance With Real World Projects
Language: English
Certificate: Yes
Duration: 6 Months
Online/Offline Available
Our Student Placed in




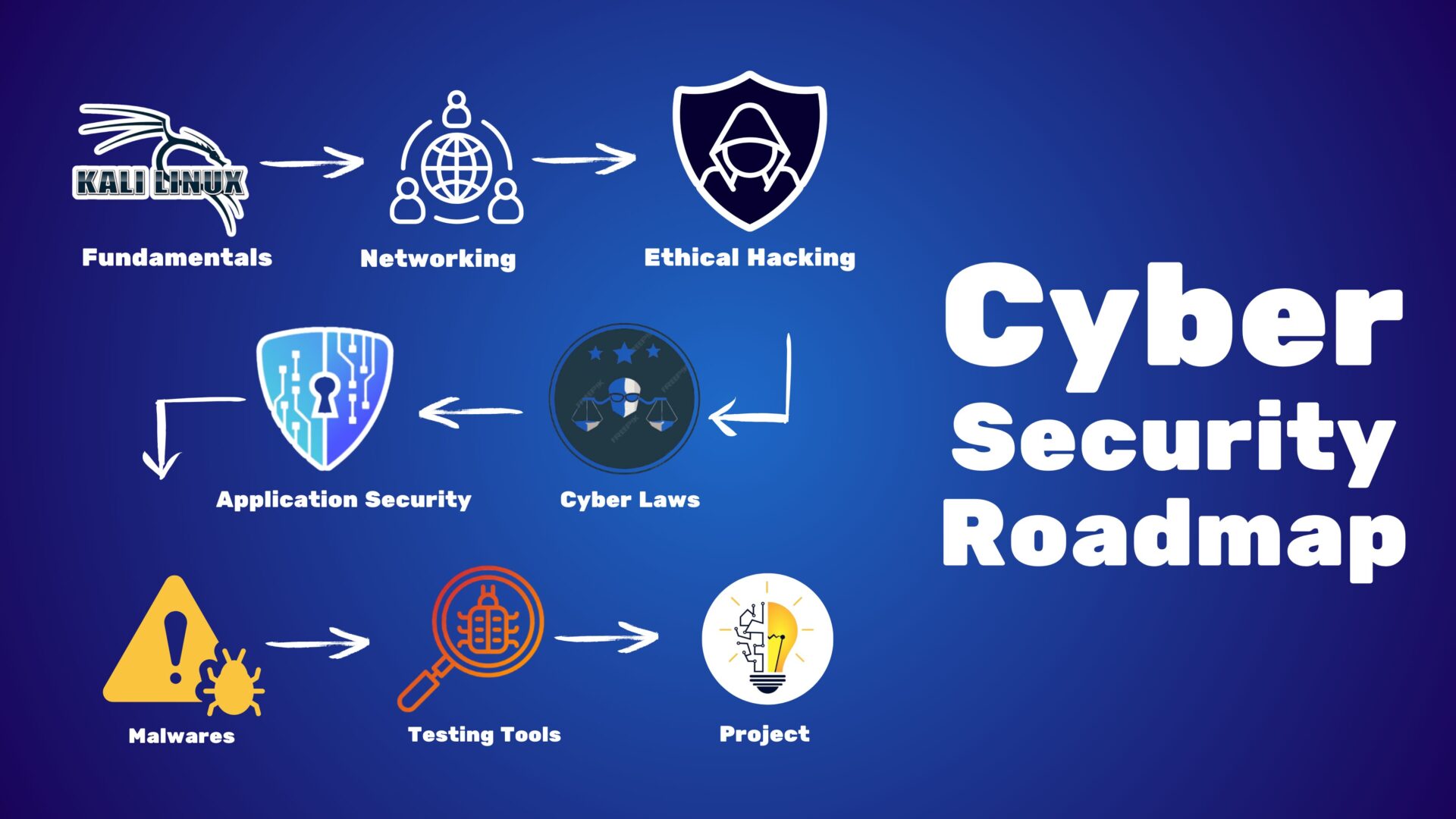
About the Course
Unlock the world of cyber security with our beginner-to-advanced course designed to help you build a strong foundation in ethical hacking, network security, and digital defense. Whether you’re a student, IT enthusiast, or career switcher, this step-by-step learning path covers real-world tools, techniques, and certifications needed to become a skilled cyber security professional. Learn at your own pace and gain the confidence to protect systems, data, and digital assets in today’s evolving cyber landscape.
What You Will Learn in Cyber Security Course
Foundation of Ethical Hacking & Information Security
Introduction to Ethical Hacking
• Introduction to HTML
• HTML Tags and Elements
• HTML –Attributes
• HTML -Formatting
• HTML –Phrase Tags
• HTML – Metatags
• HTML –Comments
• HTML-Image tags
• HTMLTables
• HTML –Lists
• HTML -Iframes
• HTML –Blocks
• HTML –Backgrounds
• HTML -Colors,Fonts
Information Gathering & Vulnerability Assessment
Denial-of-Service (DoS & DDoS)
Execution and mitigation of large-scale service disruption attacks.
Session Hijacking
Identify session hijacking methods and implement network-level protections.
Evading IDS, Firewalls & Honeypots
Bypass security infrastructure and learn how to strengthen perimeter defenses.
System Exploitation Techniques
Footprinting and Reconnaissance
Learn passive and active information gathering techniques using modern tools.
Scanning Networks
Explore different types of network scans and their countermeasures.
Enumeration
Understand detailed system information gathering methods and how to defend against them.
Vulnerability Analysis
Identify, analyze, and report vulnerabilities using industry-standard assessment tools.
Denial, Hijacking & Evasion Tactics
Footprinting and Reconnaissance
Learn passive and active information gathering techniques using modern tools.
Scanning Networks
Explore different types of network scans and their countermeasures.
Enumeration
Understand detailed system information gathering methods and how to defend against them.
Vulnerability Analysis
Identify, analyze, and report vulnerabilities using industry-standard assessment tools.
Web & Application-Level Hacking
Cloud Computing Security
Secure cloud environments, containers, and serverless applications against modern threats.
Cryptography
Encryption algorithms, PKI, digital certificates, and cryptanalysis tools explained.
Wireless, Mobile & IoT Security
Hacking Web Servers
Exploit web server vulnerabilities and defend against common attack strategies.
Hacking Web Applications
Explore OWASP Top 10, injection attacks, and secure coding best practices.
SQL Injection
Detailed SQLi attack lifecycle, evasion techniques, and database hardening.
Advanced Cyber Security Domains
Hacking Web Servers
Exploit web server vulnerabilities and defend against common attack strategies.
Hacking Web Applications
Explore OWASP Top 10, injection attacks, and secure coding best practices.
SQL Injection
Detailed SQLi attack lifecycle, evasion techniques, and database hardening.
Hands-On Learning Labs
Simulated Cyber Attacks
Learn by doing – from phishing to brute force and malware analysis.
Live Threat Detection
Use real tools like Wireshark, Burp Suite, and Metasploit to track, detect, and defend.
Red Team vs Blue Team Challenges
Experience ethical hacking and incident response in action.
Tool-Based Labs
Practice on virtual machines with Kali Linux, SIEM systems, firewalls, and more.
Skill Progress Tracker
Monitor your performance and improve with feedback after each lab.
Aptitude
Quantitative Aptitude
- Average
• Percentage
• Profit and Loss
• Simple Interest
• Compound Interest
• Ratio Proportion
• Time and Work
• Time
• Speed
• Distance Number
• System
• Permutation and Combination
• Probability
• Data Interpretation
Logical Reasoning
- Blood Relation
• Direction sense
• Coding and decoding• Clocks and Calendar• Cubes and Dices
• Seating arrangement
• Syllogism• Data sufficiency
• Puzzles
• Miscellaneous
Softskills
- Setting the tone
• Introduction of Be Employable
• Competency Matrix
• Effective Communication
• Presentation skills
• Business Communication
• Attitude + Motivation
• Emotional Intelligence
• Leadership
• Create CV/Resume
• Group Discussion
• Mock Group Discussion
• PI practice
• Virtual Interview
• Industry Knowhow and future, Certifications and
action plan
Projects
Learning Labs
• 100% virtualization for a complete learning experience
• After login, you will have full access to preconfigured targets, networks,
and the attack tools necessary to exploit them:
• Pre-configured vulnerable websites
• Vulnerable, unpatched operating systems
• Fully networked environments
• 3,500+ hacking tools And much more!
• Wide range of target platforms to hone your skills
• 519 attack techniques
• Objective-oriented flags for critical thinking and applied knowledge
assessment
• Cloud-based cyber range






FAQs
Who can enroll in this Cyber Security Course?
This course is ideal for beginners, students, IT professionals, and anyone interested in learning ethical hacking, network defense, and cyber security fundamentals. No prior coding or cybersecurity experience is required.
What skills will I gain from this course?
You’ll learn skills in ethical hacking, vulnerability assessment, malware analysis, web and mobile app security, cloud security, cryptography, and much more. The course follows a practical, hands-on approach to make you job-ready.
Is this course suitable for beginners?
Yes! The course starts from the basics and gradually progresses to advanced concepts. Each module is explained in a simple and easy-to-understand way, making it perfect for beginners.
Will I get a certificate after completing the course?
Yes, you will receive a certificate of completion that can enhance your resume and help showcase your cybersecurity skills to potential employers or clients.
What tools and technologies will I learn?
You will get hands-on experience with tools like Nmap, Wireshark, Metasploit, Burp Suite, Nessus, SQLMap, John the Ripper, and more widely used in the cybersecurity industry.
Are there any live sessions or is this a self-paced course?
The course is designed to be flexible and self-paced. However, there may be occasional live sessions or doubt-clearing sessions depending on the platform and batch availability.
Can this course help me build a career in cyber security?
Absolutely! This course covers essential topics that align with industry needs. It can help you pursue roles like Ethical Hacker, Security Analyst, Penetration Tester, SOC Analyst, and more.
Do I need a technical background to join?
Not necessarily. While having a basic understanding of computers and networks is helpful, the course is designed to guide you step-by-step, even if you’re from a non-technical background.
Will I get practical, hands-on experience?
Yes, the course includes real-world simulations, practical labs, and exercises so you can apply what you learn in actual cybersecurity scenarios.
How long will it take to complete the course?
Depending on your pace, the course can typically be completed in 8 to 12 weeks, especially if you dedicate a few hours per week consistently.

Earn a Master Certification in Cyber Security
Get recognized for your expertise with a Master Certification in Cyber Security. This industry-recognized certificate validates your skills and makes you stand out in the job market.
